
Published by Chief Editor, Sammy Campbell. Written by Mark Pullen.
I swore we wouldn’t published another article on Hillary Clinton’s mishandling of classified information scandal. After all, it’s 2019 and the two-tiered justice system that still exist, is old news. However, my job is to review testimony transcripts. I’m on Trisha Anderson’s testimony, she was a lawyer for the FBI in the National Security Division.
Here is her testimony that struck me. My comments will be in bold, within her testimony.
Q I guess if — what I’m trying to understand is, if there was a real problem with regard to the particular statute in either the FBI’s legal analysis, or the Department’s legal analysis, with respect to that particular statute, why are FBI agents submitting affidavits that are relying upon a particular statute that has real potential legal problems, according to the DOJ analysis?
A So, as I explained before, there are potentially specific prosecutions that could theoretically be brought that might result in constitutional concerns. However, the statute is not constitutionally invalid on its face and there are many prosecutions that could be brought, theoretically, where intent is proven that would not pose constitutional problems. So, for example, in this particular case, had we had evidence of intent, it’s theoretically possible that we could have brought a prosecution, might have brought a prosecution under that statute. I’m not saying that’s, you know, what would have happened necessarily, but the statute is not — it is not the Department’s view, as I understand it, the statute is invalid for constitutional reasons in every circumstance.
Q Did you believe that the statute required intent?
A That was my understanding of the Department’s interpretation, yes. {Meaning the (f) section to this statute was deemed unconstitutional by Lynch because section (f) didn’t have the word, intent, in it. Loretta Lynch confirmed this in her testimony. However, I will show this is the first shell in the shell-game in the fraud of Comey and Lynch. In this report, DOJ/FBI: We show how-why Hillary & others should’ve been prosecuted. we do prove that Hillary Clinton showed intent to break the law.}
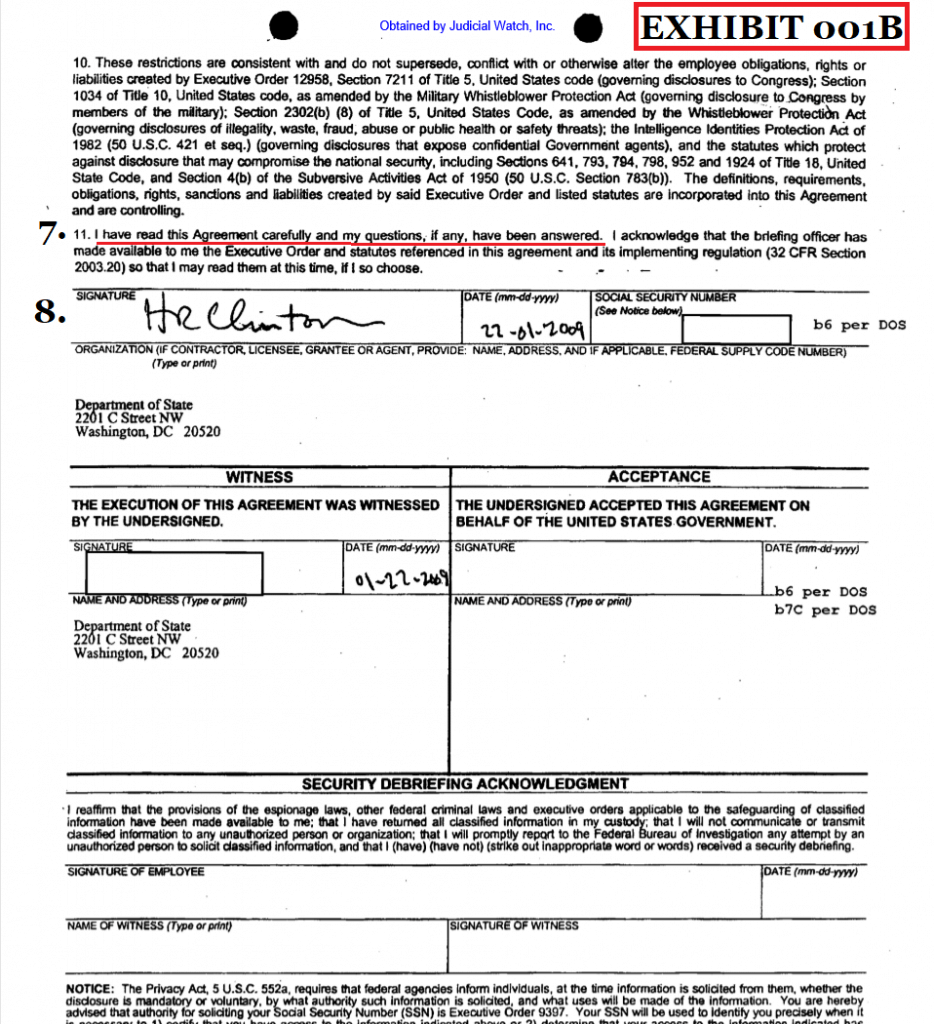
Q Knowledge would not have been — knowledge of the fact that passage of classified information over unsecure means would not have been one of the elements of an offense under 793? {The security clearance document that Clinton signed, had the 793 statute listed with other statutes.}
A So I don’t know. I’m not an expert in this area. I was not the lead lawyer on this case.{She was a supervisor for lawyers in the National Security Division of the FBI, and she can’t say, the sending of classified information over unsecured means is a breach of U.S. law? So in effect, Anderson is saying she might do the same thing by mistake or with intent. Anderson did sign the same security clearance document for her own security clearance.}
Q But I think you had testified previously that you consider yourself a national security expert. And this particular investigation is going through the Counterintelligence Division, as you indicated. And mishandling investigations, to my knowledge, are not few and far between, that the Department and the FBI are relatively accustomed to these types of investigations. So what I’m trying to understand is, if you have a statute that is often used by the FBI, you and your attorneys, I would think, would be relatively knowledgeable about the use of that particular statute.
A So, as I testified, 793(f) has never been used, to my understanding. In fact, I’m not sure it was my testimony, but I think I agreed in response to a question that Mr. Baker asked me. So 793(f) has never been used before.{This statute has been used before, mainly to charge military personnel. The DOJ allowed the FBI to use this statute to secure warrants for Clinton’s server(s) and Anthony Wiener’s laptop computer. Anderson’s testimony appears to be, if a statute hasn’t been used before for prosecution, then it can’t be used. So, how does a new bill apply to anyone that Congress passes and sends to the President to be signed into a law?}
Q Are you aware of other —
A I really don’t know how many occasions the issue has ever come up where there could be a fact pattern that was discussed and considered. But more broadly, my job responsibilities included overseeing the legal support to the — to — legal advice provided to the FBI on all counterterrorism investigations, counterintelligence investigations, and cyber investigations. And so no, I was not an expert on — on the specific category of mishandling violations or the particular statutes at issue. That was not my job. My job was to oversee those lawyers, those experts who handled those issues. And one of those experts was the lawyer who worked for me on that — on the Midyear Exam case.
Q So are statutes only good if they are used?
A I don’t know what that means.{Wow!}
Q You just indicated that the statute had never been used. So does that, the fact that the statute — and I am not stipulating to that. But in the FBI’s analysis, I presume, the statute that you are referring to in terms of gross negligence had never been used. So what I am asking is, does that mean that statutes that are never used are no longer good law?
A No, not at all. That’s not — I was just trying to — you had — I thought you had misinterpreted what I had said in your question, and I was trying to —
Q No. I think if part of the legal reasoning as to why the gross negligence statute was not used in terms of a potential prosecution of Mrs. Clinton, if one of the — if part of that rationale was that it had never been used, then, by extension, one might presume that other statutes that are on the books, if they aren’t being used, should not be ever considered as predication for a prosecution.
A That’s not — that was not the intent of my statement.
Please take the time to read the entire content of this document. At number four, you can see that statute 793 is listed among other statutes. We see 793 listed for five and six. Clinton had thousands of classified documents on her server(s) after she left government employment.

18 U.S. Code § 793
(a) Whoever, for the purpose of obtaining information respecting the national defense with intent or reason to believe that the information is to be used to the injury of the United States, or to the advantage of any foreign nation, goes upon, enters, flies over, or otherwise obtains information concerning any vessel, aircraft, work of defense, navy yard, naval station, submarine base, fueling station, fort, battery, torpedo station, dockyard, canal, railroad, arsenal, camp, factory, mine, telegraph, telephone, wireless, or signal station, building, office, research laboratory or station or other place connected with the national defense owned or constructed, or in progress of construction by the United States or under the control of the United States, or of any of its officers, departments, or agencies, or within the exclusive jurisdiction of the United States, or any place in which any vessel, aircraft, arms, munitions, or other materials or instruments for use in time of war are being made, prepared, repaired, stored, or are the subject of research or development, under any contract or agreement with the United States, or any department or agency thereof, or with any person on behalf of the United States, or otherwise on behalf of the United States, or any prohibited place so designated by the President by proclamation in time of war or in case of national emergency in which anything for the use of the Army, Navy, or Air Force is being prepared or constructed or stored, information as to which prohibited place the President has determined would be prejudicial to the national defense; or
(b) Whoever, for the purpose aforesaid, and with like intent or reason to believe, copies, takes, makes, or obtains, or attempts to copy, take, make, or obtain, any sketch, photograph, photographic negative, blueprint, plan, map, model, instrument, appliance, document, writing, or note of anything connected with the national defense; or
(c) Whoever, for the purpose aforesaid, receives or obtains or agrees or attempts to receive or obtain from any person, or from any source whatever, any document, writing, code book, signal book, sketch, photograph, photographic negative, blueprint, plan, map, model, instrument, appliance, or note, of anything connected with the national defense, knowing or having reason to believe, at the time he receives or obtains, or agrees or attempts to receive or obtain it, that it has been or will be obtained, taken, made, or disposed of by any person contrary to the provisions of this chapter; or
(d) Whoever, lawfully having possession of, access to, control over, or being entrusted with any document, writing, code book, signal book, sketch, photograph, photographic negative, blueprint, plan, map, model, instrument, appliance, or note relating to the national defense, or information relating to the national defense which information the possessor has reason to believe could be used to the injury of the United States or to the advantage of any foreign nation, willfully communicates, delivers, transmits or causes to be communicated, delivered, or transmitted or attempts to communicate, deliver, transmit or cause to be communicated, delivered or transmitted the same to any person not entitled to receive it, or willfully retains the same and fails to deliver it on demand to the officer or employee of the United States entitled to receive it; or
(e) Whoever having unauthorized possession of, access to, or control over any document, writing, code book, signal book, sketch, photograph, photographic negative, blueprint, plan, map, model, instrument, appliance, or note relating to the national defense, or information relating to the national defense which information the possessor has reason to believe could be used to the injury of the United States or to the advantage of any foreign nation, willfully communicates, delivers, transmits or causes to be communicated, delivered, or transmitted, or attempts to communicate, deliver, transmit or cause to be communicated, delivered, or transmitted the same to any person not entitled to receive it, or willfully retains the same and fails to deliver it to the officer or employee of the United States entitled to receive it; or
(f) Whoever, being entrusted with or having lawful possession or control of any document, writing, code book, signal book, sketch, photograph, photographic negative, blueprint, plan, map, model, instrument, appliance, note, or information, relating to the national defense, (1) through gross negligence permits the same to be removed from its proper place of custody or delivered to anyone in violation of his trust, or to be lost, stolen, abstracted, or destroyed, or (2) having knowledge that the same has been illegally removed from its proper place of custody or delivered to anyone in violation of its trust, or lost, or stolen, abstracted, or destroyed, and fails to make prompt report of such loss, theft, abstraction, or destruction to his superior officer—
Shall be fined under this title or imprisoned not more than ten years, or both.
(g) If two or more persons conspire to violate any of the foregoing provisions of this section, and one or more of such persons do any act to effect the object of the conspiracy, each of the parties to such conspiracy shall be subject to the punishment provided for the offense which is the object of such conspiracy.
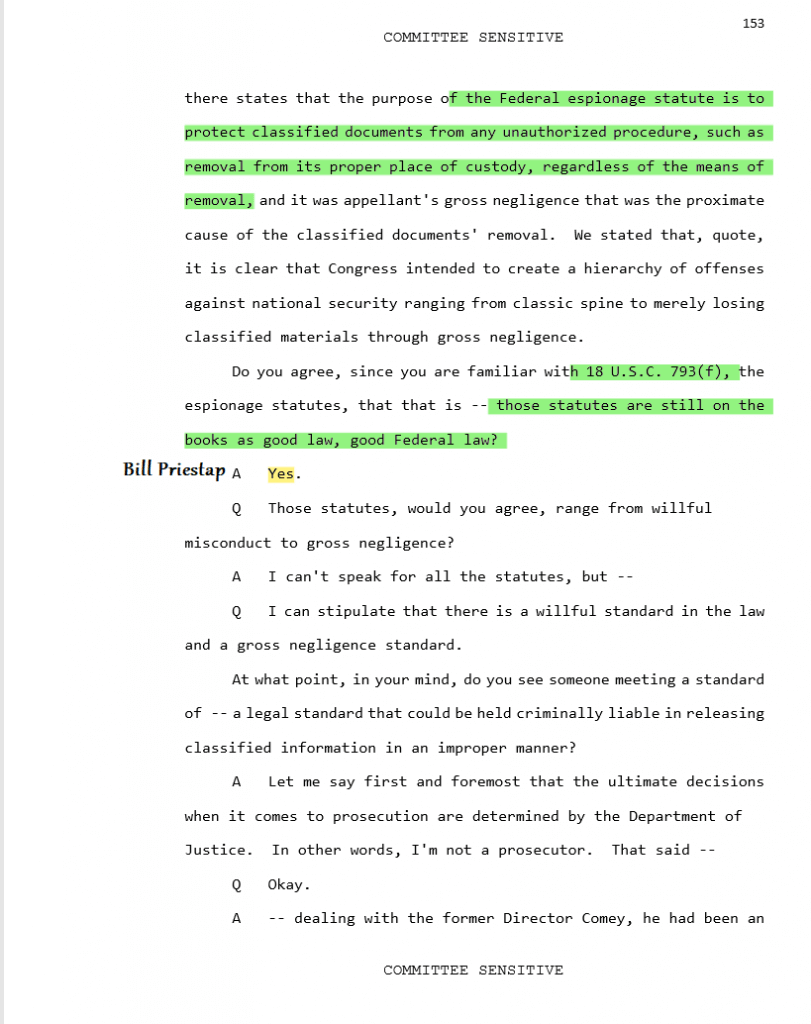
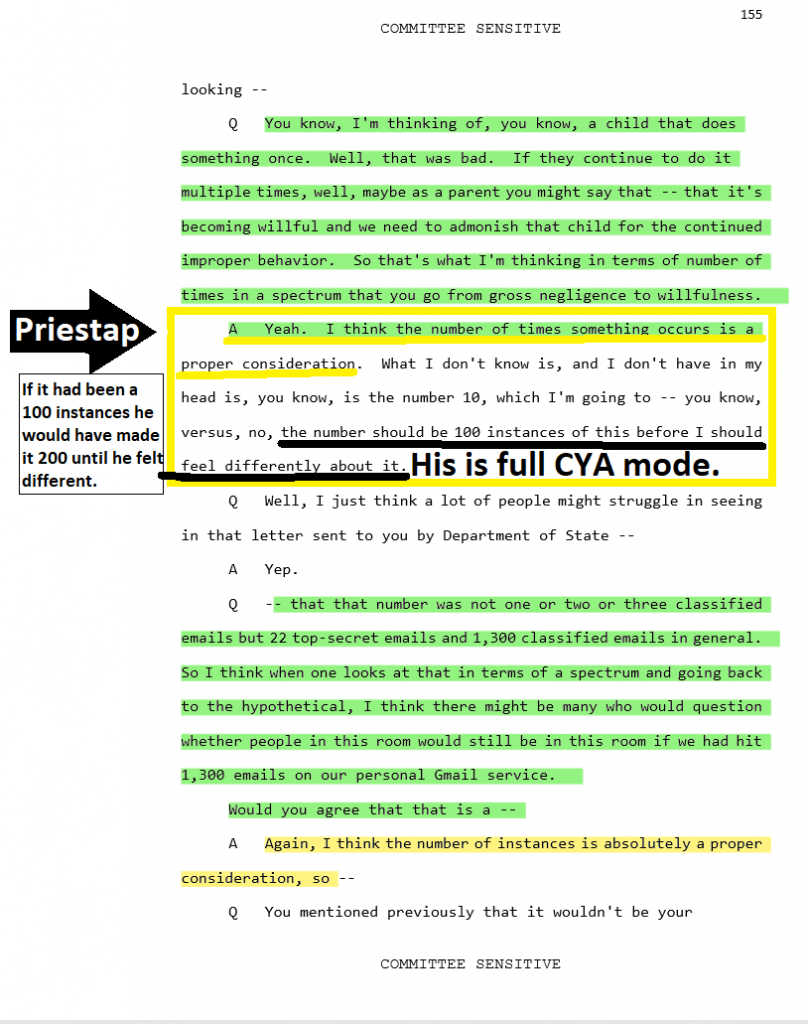
Bill Priestap headed the Clinton investigation. Peter Strzok answered to him. Priestap concedes 18 U.S. 793 (f) is good law, however, you can see, he is all to happy to move the goal-post as Comey did during his testimony after his exoneration presser for Hillary Clinton.
It would be an error to underestimate James Comey. I have come to believe he is a great strategic thinker. His only weakness is his hubris. Comey brought his professor friend as a special FBI employee during the Clinton investigation. The professor received a security clearance. According to Comey’s chief of staff, James Rybicki, Comey had never before brought on a special employee before. This is the same person that Comey leaked his classified memos to, with the direction to read excerpts from the memos to the media. Comey knew there was a possibility that he would be fired by either Trump or Clinton, thus, he set the pieces in place to strike back at President Trump over a year before he was fired. Comey had a plan if Hillary Clinton had won the election. Comey had a binder in his office safe that was marked as TOP SECRET-Clinton emails. Comey on his first draft of the exoneration statement included the wording, gross negligence, to describe Clinton’s handling of classified information.The wording was changed to, careless. I purpose this was Comey thinking four moves ahead. It is possible that he anticipated someone in Congress would demand his original draft. Comey purposely put gross negligence in the draft to steer attention toward section (f) of statute 793. So, this is another shell with intent, and section (f).
Hillary Clinton violated other statutes and sections of 793 and that’s what had Comey and Lynch running scared. Not once during any testimony, has someone brought up other sections of 793 or other statutes. If you were to guess what term the shell game is hiding and you guessed guilt, then you be wrong. The term is SCIF for Sensitive Compartmented Information Facility. By hiding this, Comey and Lynch hid the Indefensible. Clinton did leave this room at her two homes open so three people with no security clearance could enter the SCIF rooms to read, copy, and collect the classified documents that were sent to the SCIF rooms via a secure data line. This distraction was so effective that not once did any Congressperson question Comey or Lynch on these occurrences. Nor was this mentioned in the Inspector General’s report.